Sometimes risk is compensated with opportunity” – this statement is true for any business. However, when it comes to “cloud” the opportunity is enormous that it’s worth facing the risks through proper mitigation and planning.
This purpose of this blog is to enlighten the readers on the security areas to concentrate and plan to nullify the risks and reap the cloud opportunity to the fullest extent possible. (Also know about the consideration to be taken while migrating).
Security Threat Trend
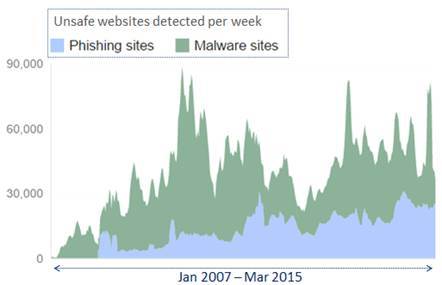
While technology has been evolving rapidly, there has been a proportionate increase in the security threats. The graph you see on this slide is taken from google transparency report, which keeps track of the various security incidents that are happening across the globe. As you can see, there has been a steady increase in the count of phishing and malware sites.
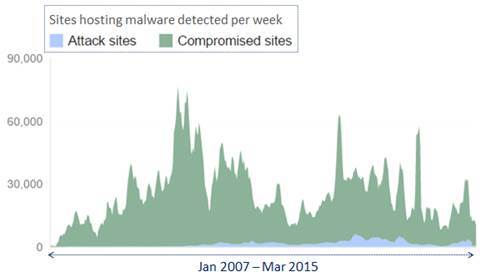
This one shows the trend in number of compromised sites over the years. If you had noticed the recent years, unlike the earlier years there is a surge pattern, which indicates that the attacks are more focused and severe in nature.
Major Data Breaches in Cloud
2015
- In February 2015, Anthem suffered a data breach of nearly 80 million records.
2014
- In August 2014, nearly 200 photographs of celebrities were posted to the image board website 4chan.
- In September 2014, Home Depot suffered a data breach of 56 million credit card numbers.
- In October 2014, Staples suffered a data breach of 1.16 million customer payment cards.
2013
- In October 2013, Adobe Systems revealed that their corporate data base was hacked and some 130 million user records were stolen.
- In late November to early December 2013, Target Corporation announced that data from around 40 million credit and debit cards was stolen.
There is one other dimension to the security aspects involved in delivering a solution in cloud. Here are some of the recent incidents where customer’s data have been shared with others as part of a legal compliance. Well, I don’t want to call this as a threat, but definitely something that SaaS providers should be aware of.
By the way, if you think this is the case only with Microsoft and staying away from Microsoft will solve the issue, then you are wrong.
I believe most of you must have heard about the patriot act. According to US patriot act, companies based anywhere in the world, provided they have a US parent company, have to disclose information about their customers to US law enforcement, and this happens without the knowledge or consent from the customer. This is why it is critical that SaaS ISVs choose a cloud provider knowing exactly which legislation they and you have to comply with and know your risks.
Again, Does this mean staying away from US will solve the issue? Not at all.
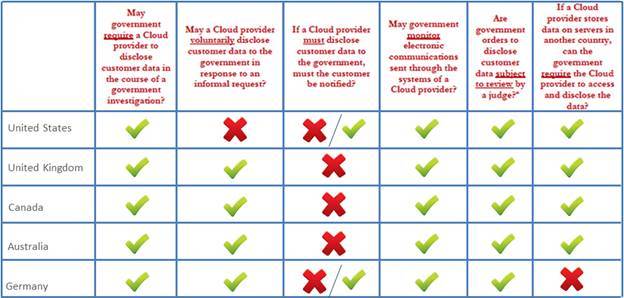
Let’s take a look at how this unfolds for some of the key regions in the world.
As you can see the policies are pretty much similar across all the major regions in the world. Therefore, it’s upto the solution provider to build a robust and secure system that can overcome these security threats and challenges.
- Top 10 NFR in Software Architecture – Part 1 - December 1, 2022
- Top 10 Critical NFR for SaaS Applications – Part 2 - October 20, 2022
- Why enterprises should standardize Digital Application Management - July 17, 2017








Comments