Why are hackers attacking ecommerce sites?
As more businesses suffer severe security breaches, the wave of compromised data rises. According to data breach statistics, hackers are strongly motivated by money to obtain data, and personal information is highly valued data to infiltrate. Although breaches are getting more prevalent, businesses are still not adequately prepared.
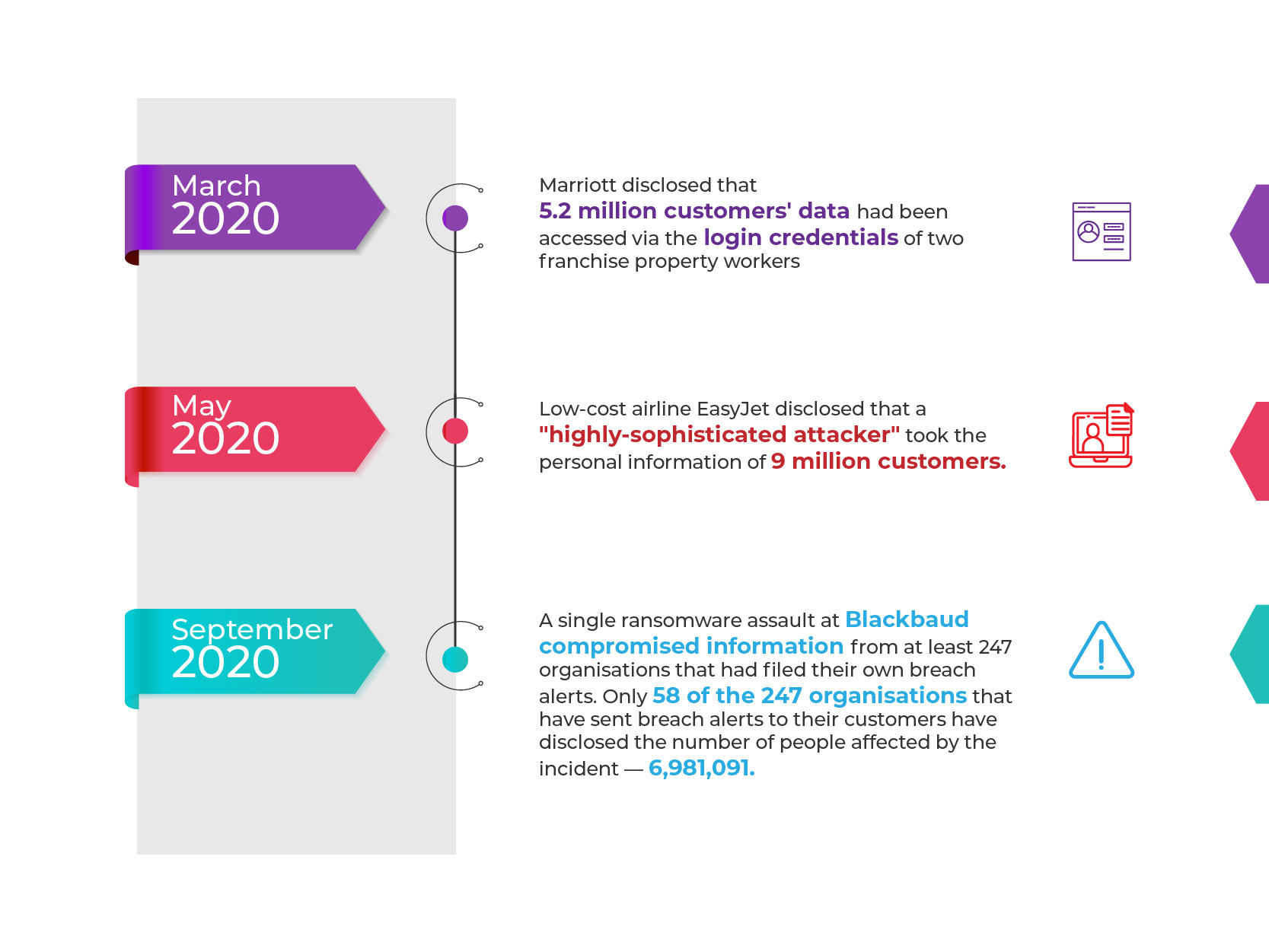
A few recent data breaches include:
The statistics presented above have major ramifications for retailers, particularly since trust and customer faith in your brand are the only ways to secure success. The best way to secure an online or ecommerce business is to incorporate best practices that guarantee cyber security from the beginning. New platforms, solutions, and application-based infrastructures entail new ways of thinking.
In this article, we’ll discuss some of the most common security issues that retailers should be aware of. Many e-commerce security risks are universal, regardless of whether you’re utilising third-party platform channels through headless commerce implementations or creating your own microservices.
Understanding e-commerce security threats
Because of their complexity, headless architectures require more security and trust than standard commerce solutions. These are the most prevalent security issues that must be addressed as businesses introduce new patterns in headless applications:
Shopper Authentication
One of the most common vulnerabilities is shopper and API authentication, which is caused by a lack of control over the environments in which mobile and single-page apps run. It is vital to improve authentication. Consider the potentially devastating impacts of a hacker gaining access to a customer’s identification code to connect to their mobile banking app.
Mobile apps require direct API calls into the commerce platform because they are built for app stores. For authentication, these direct API requests user or client credentials. It is crucial to avoid unsafe solutions such as keeping client or user credentials on the device itself. Single-page apps must meet comparable security standards.
The idea is to employ secure APIs for shopper login. These APIs have pre-built, secure processes based on standards like OpenID Connect (OIDC) and OAuth, which help to prevent vulnerabilities in shopper authentication and API access.
Personal Data Protection
Customers demand personalized experiences across platforms, yet just 27% fully grasp how businesses utilise their personal information. It is critical to select a commerce platform that complies with regional privacy standards such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA). You must closely adhere to these requirements to guarantee that data is stored in the relevant area and that consent management is implemented in your headless architecture.
Storefront
Following Open Web Application Security Project (OWASP) recommended practices, using a web application firewall (WAF), monitoring for denial-of-service attacks (DDOS), and avoiding cross-site scripting (XSS) attack vectors are all necessary for any type of storefront. APIs should be accessed using HTTPS network connections. APIs must be protected with robust authentication on every call, and client data should be encrypted on disc at rest.
Here are few best practices to consider!
People
While your storefront is being designed by a solution architect and built by a software developer, a security engineer guarantees that all of your hard work — and the money it brings in — is safe from attacks.
Security engineers employ a multi-layered protection strategy. They create security rules, investigate issues, and manage everything from penetration testing to vulnerability scanning. If you’re creating your own storefront, it’s up to your team to protect your front-end display layer against malicious assaults and breaches throughout development and operations.
In fact, if you purchase an out-of-the-box headless storefront with a managed runtime, you will outsource most of the ongoing operational security effort to a trusted partner. As a result, your engineers will have access to an expert who can answer queries at any time.
Process
In addition, to properly evaluating an API’s specification for security features and options, it is vital to include security into your organization’s software development lifecycle (SDL).
The goal is to run a security threat model at the design phase to guarantee that coding gets off to a good start. Many elements of the design will require security measures to be programmed in throughout the development process. As development progresses, a final code review and penetration testing should round up the process, all of which should be done in collaboration with your security engineers, who will provide guidance every step of the way.
Platform
With headless commerce, information flows in and out of your website. That is why it is critical to have a commerce platform that enables safe, user identity-led access to shopper APIs. Developers utilise the Shopper Login and API Access Service (SLAS) with a platform like Commerce Cloud to enable safe access to shopper APIs through a high-scale authentication and authorization solution. You may create multiple security and authentication models for customers and retailers, as well as trusted systems on their behalf.
These include the flexibility to shop from anywhere using multiple OAuth and OIDC login processes on a desktop, a mobile app, or a browser-based app. “Trusted system” and “agent on behalf of” processes allow businesses to use design patterns to proxy prior occurrences, such as a shopper’s phone order. Commerce Cloud also allows you to establish and maintain API clients, giving your team complete control over the scope of access for consumers and administrators.
Finally, Commerce Cloud provides you with a controlled runtime for your storefront. This is the system that hosts, scales, and secures your shop. It contains automatic monitoring to reduce DDOS attacks as well as a web application firewall (WAF) to prevent hackers from gaining access. Furthermore, it maintains physical data centre and hardware security, as well as frequent security upgrades to address key vulnerabilities.
Get more tips on going headless.
- Salesforce B2C Commerce Cloud: What’s new In 22.4 - May 12, 2022
- Why is BOPIS still a problem for retailers? How can Salesforce Commerce Cloud help? - April 26, 2022
- 7 Reasons to Choose Oracle Retail Merchandising System Over JDA MMS - April 20, 2022









Comments